If the internet is a city, mobile apps are its busiest intersections. You wake up and open a fitness app to work out, book a ride to work through a ride-hailing app, and order lunch from a food delivery app, all before 1 PM. Whether you’re shopping, commuting, or winding down with entertainment, apps have taken over every part of daily life.
In fact, mobile apps alone generated over $935 billion in revenue in 2024, showing just how central they’ve become to both consumer behavior and business growth.
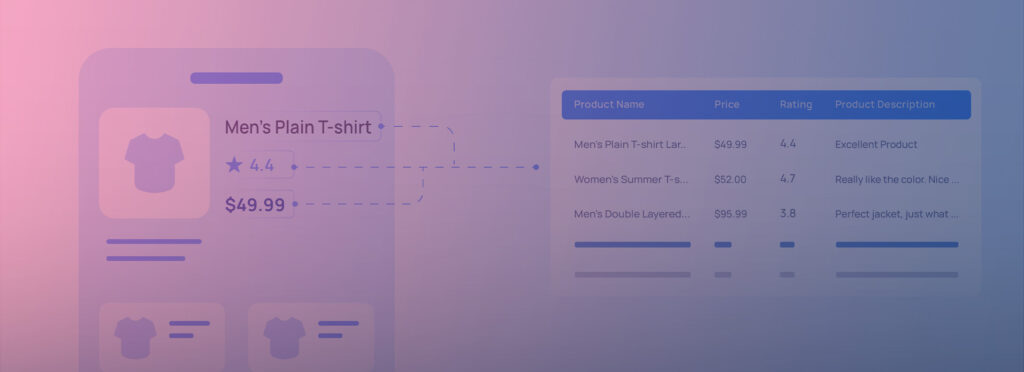
As more user activity shifts to mobile, a growing volume of valuable data like pricing, availability, popular locations, and product details now lives exclusively within app ecosystems. This data is critical for businesses looking to stay competitive, optimize strategies, or monitor markets in real time.
But accessing that data isn’t as easy as it sounds. Unlike websites that serve up content through easily accessible HTML, mobile apps retrieve their data through hidden APIs and compact data formats. Plus, the data often travels through encrypted channels.
So, the process of extracting data from a mobile application (known as app scraping) requires a more advanced approach. They are: identifying API endpoints, handling authentication tokens, and navigating security features like SSL pinning and device fingerprinting that are built to prevent external access.
Nonetheless, there are workarounds with the right techniques and tools that make it possible to reveal the data hidden beneath the surface.

Mobile apps hide data behind walls
Unlike websites, where you can right-click, inspect content, and network in your browser, like the HTML, URLs, and image sources, mobile apps don’t make their data this easily visible. Everything the user sees in an app, like restaurant lists, prices, ratings, etc., is hidden and could even be encrypted. They can be accessed only by using an emulator and interceptor software after enabling root permission and ADB debugging on the device that is going to be used.
The walls that help in hiding data are a combination of:
No URLs or HTML – You can see the structure of a website by inspecting the page since they are built on HTML, but not a mobile app. Apps don’t have URLs or HTML, so there’s no page source to inspect.
API-based data transfers – Mobile apps use APIs to fetch data in the background from the server. They are private and cannot be accessed outside the app.
Non-standard data formats – Apps often use unstructured formats of data like JSON and Protobuf. They aren’t visible on the user’s side of the UI and pass secretly between the app and the server.
High encryption and security – Many apps implement SSL pinning, token rotation and device validation, which make it difficult for scrapers to intercept or replicate the app’s data requests.
Challenges in mobile apps scraping
Now that we know how mobile apps hide, protect, and encrypt their data.
Let’s look at how they act as real challenges in mobile app scraping.
Mobile-specific data structures
Apps rely on formats that are optimized for speed and efficiency, but they are harder to work with. Such as:
- JSON – A common but deeply nested and sometimes wrapped in unexpected structures.
- Protobuff – (Protocol Buffers) compresses data into binary, which makes it unreadable without using decoding tools.
- Custom Encryption – Some apps even use custom encryption to scramble data in transit.
So, even if you capture the data, you still need to decode and restructure it before it’s usable.
Hidden and Complex APIs
Apps normally don’t reveal their API documentation, so you have to reverse-engineer it. Even then it’s not always simple to extract data because:
- Apps use gRPC, which bundles requests in binary form over HTTP/2, which is hard to intercept.
- They rely on WebSockets for real-time updates, meaning the connection stays open and constantly streams data.
- Headers frequently include authentication tokens, device identifiers, and signatures that change frequently.
Replaying an API call outside the app isn’t as easy as copying a URL, so you have to mimic everything the app does.
Multiple layers of security
Apps are designed to resist outside access. Their security mechanisms are stricter than those of websites.
- SSL pinning blocks proxy tools from capturing traffic.
- Dynamic tokens expire quickly or are tied to specific devices or sessions.
- Device fingerprinting checks for consistency in app version, OS, and even screen size.
- Some apps obfuscate their code, making it hard to understand how they generate or structure requests.
Each of these defenses adds friction to scraping, and most apps use several at once.
Grepsr’s Approach to App Scraping
To scrape mobile applications, you need to simulate a real mobile device very accurately, sometimes even down to the OS version, screen resolution, and app version.
Grepsr specializes in solving exactly these kinds of challenges. We have ample experience in reverse-engineering mobile app data flows, intercepting secure API traffic, and delivering clean, structured datasets. All without needing your internal team to touch a proxy or emulator.
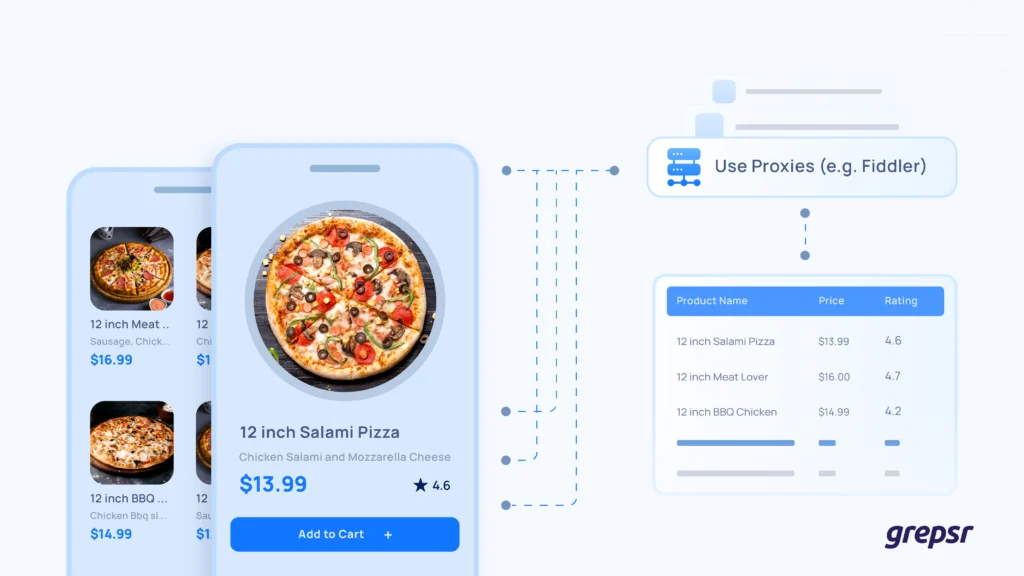
The techniques that we implement are:
API Interception
We monitor how the app communicates with its server, capturing API calls using tools like Fiddler. Once we identify the requests that carry the data, such as product lists and prices, we replicate them programmatically to fetch the same data directly from the source without the app interface.
Reverse Engineering
For apps that don’t expose APIs openly, we analyze the app’s code (APK on Android or app binaries on iOS) to uncover hidden endpoints, request formats, and parameters. This helps us understand how the app structures its communication so we can recreate it externally.
Authentication Handling
Apps often use rotating tokens or device-specific credentials to block unauthorized access. We manage this automatically, handling login flows, session refresh, and token rotation so data extraction stays seamless and uninterrupted.
Automated Workflows
Whether data is accessible through API calls or only through on-screen elements, we set up automated processes to collect, clean, and deliver it. For that, we replicate user interactions using tools like UI Automator. These tools simulate user actions like clicking buttons and navigating the app interface. The automated scripts capture data directly from the GUI.
What You Get with Grepsr
In delivery apps, data like restaurant availability, pricing, and delivery times can reveal powerful market insights, but it’s difficult to access. However, Grepsr can take care of all the heavy lifting so you don’t have to navigate the technical maze of mobile app scraping.
Here’s what you get if you partner with Grepsr.
- Structured datasets from apps that can’t be scraped with browser tools alone
- Support for login flows, geo-fenced content, session tokens, and device-bound data
- Automated extraction and delivery, where you can choose the format (CSV, JSON, API), we handle the rest
- Security compliance and stability without dealing with SSL pinning, token refresh, or IP blocks.
- A fully managed service where you don’t need to worry about infrastructure to maintain, scripts to debug, or blockers in your workflow.
Let us help you turn mobile app interfaces into reliable, structured datasets—delivered where and how you need them. Get started with Grepsr.